Integrating Control Center with Okta OpenID Authentication Server
This tutorial walks you through the process of integrating Control Center with Okta OpenID. OpenID is an open-standard, decentralized authentication protocol. It enables users to authenticate to collaborating sites that use third-party services. Thus, it eliminates the need for webmasters to provide their own login systems and enables users to log in to multiple unrelated websites without providing a unique identifier and password for each site. GridGain Control Center supports this mechanism. Control Center can be configured to use third-party authentication servers such as Google and Okta. We chose Okta for this tutorial because Okta provides a development environment that is free and can be used for testing.
OpenID Authentication Cluster Configuration
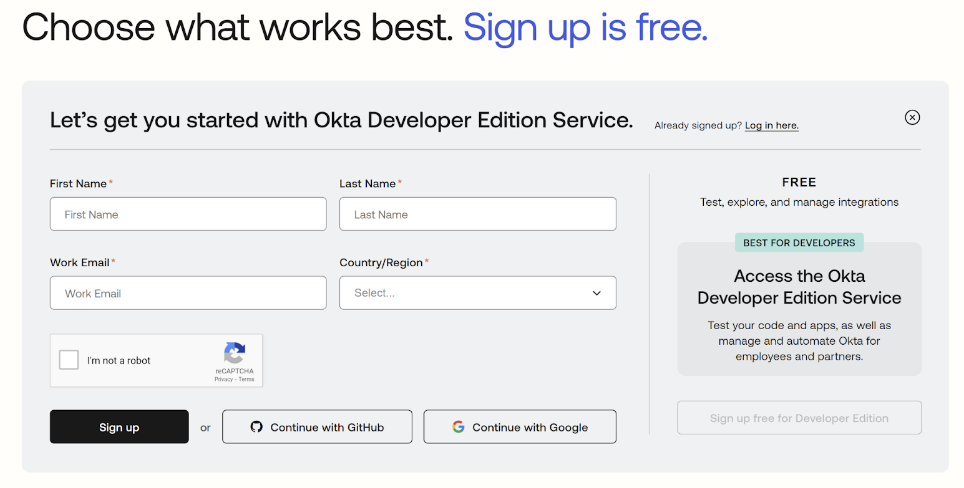
First, create your own free development account:
-
Navigate to https://developer.okta.com/signup/.
-
Complete the form.
-
Verify that you are not a robot.
-
Click Sign up.
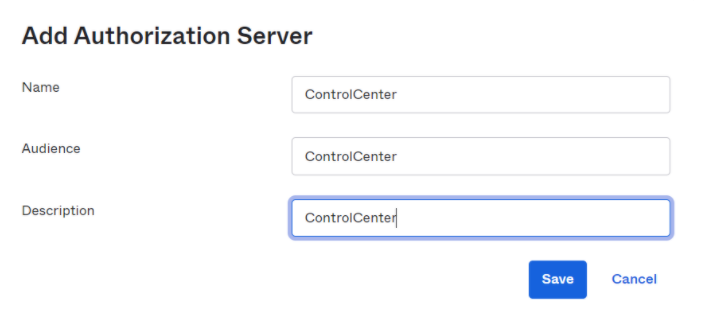
After logging in to the developer UI portal, create an authentication server:
-
Navigate to the Security menu.
-
Select the API tab.
-
Select Add Authorization Server.
-
Specify a name, audience, and description for the server.
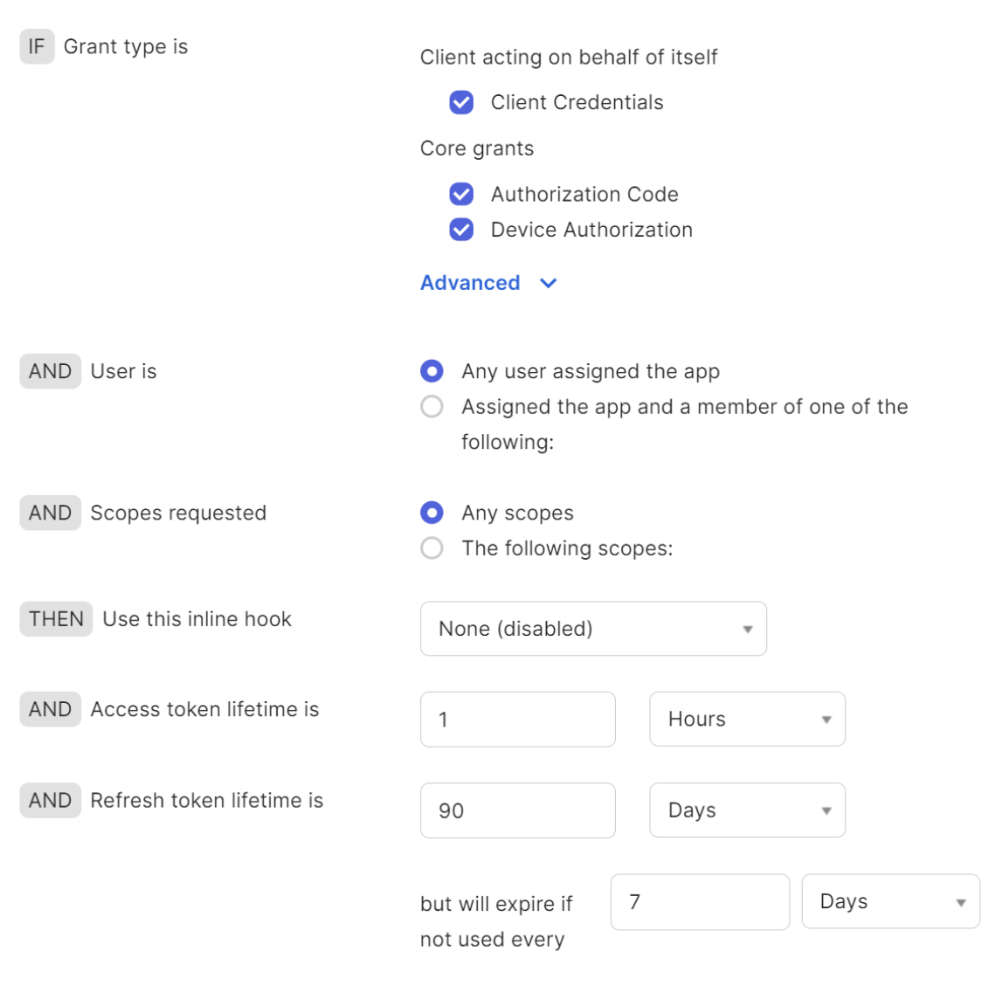
After you create the server, you must create at least one access policy. If there is no access policy, all user login attempts fail. For this test, you can use the default policy, as shown below:
For other parts of the configuration, you can also use the defaults. Then, navigate to the Settings tab and click the Metadata URI link to get authentication cluster metadata.
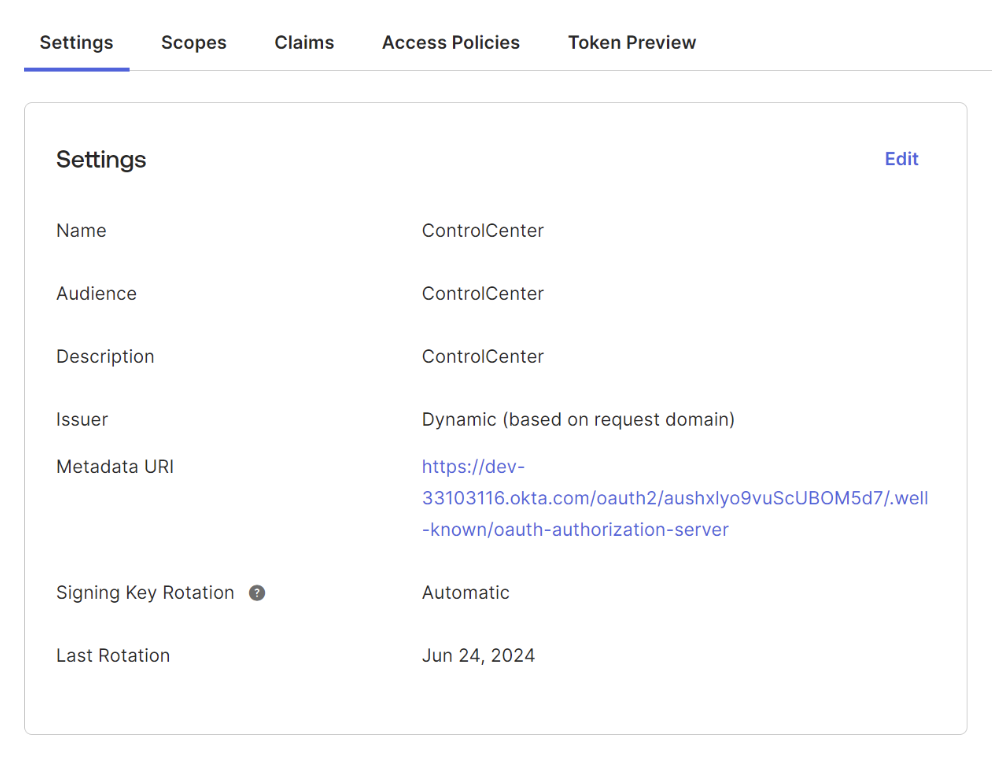
You use the metadata later, to configure Control Center. The following is a metadata output example:
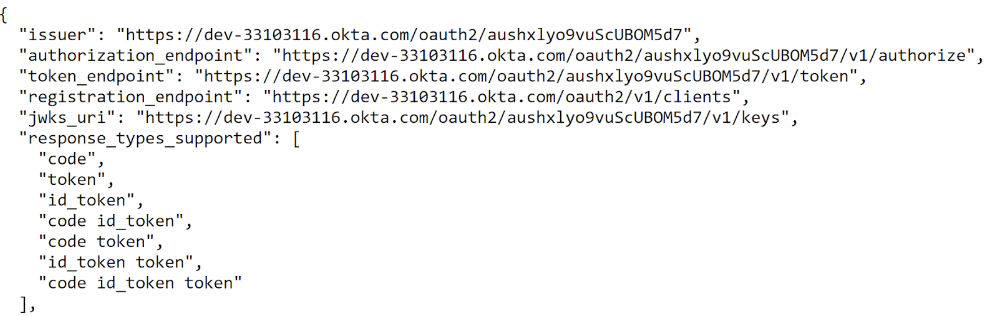
Now, create the OpenID application that is used to authenticate Control Center:
-
Navigate to the Applications menu.
-
Select the Applications tab.
-
Click Create App Integration.

-
In the Create a new app integration dialog, select OpenID Connect.
-
In the lower part of the dialog, select Native app.
-
Click Next.

-
Enter the following line in the Sign-in redirect URIs field, where you must set the Control Center host and port:
http://[Control Center host]:[Control Center port]/api/v1/oauth2/login/okta.
-
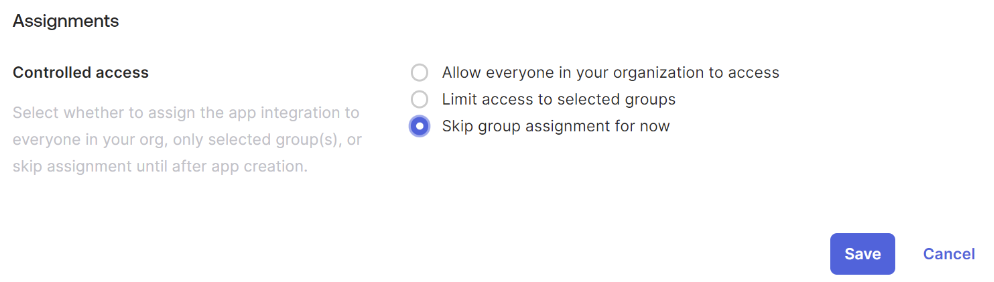
Select Skip group assignment for now.
-
Click Save.
-
In the Client Credentials screen, select the Client secret option under Client authentication.
-
Make sure the PKCE option is deselected.
-
Copy the
Client IDandClient secretvalues: you will use them for Control Center configuration.
-
Navigate to the Directory menu.
-
Open the People tab.

-
Click Add person to create a new user.

-
Open your newly created application settings and edit the Assignments list to identify the people and groups who can access the Control Center UI.

You are now ready to use the OpenID authentication to log into Control Center.
Control Center Configuration
Now, configure Control Center:
-
Download and unzip the Control Center binaries.
-
Move to the root folder of the unzipped directory and create the
application.yamlfile:spring: security: oauth2: client: registration: okta: client-id: **************************** client-secret: ***************************** provider: okta: authorization-uri: https://dev-33103116.okta.com/oauth2/aushxlyo9vuScUBOM5d7/v1/authorize token-uri: https://dev-33103116.okta.com/oauth2/aushxlyo9vuScUBOM5d7/v1/token jwk-set-uri: https://dev-33103116.okta.com/oauth2/aushxlyo9vuScUBOM5d7/v1/keys -
Start Control Center using the
control-center.shscript -
Navigate to the Control Center UI and click Sign in button:

-
Make sure that you are logged off in the Okta developer portal.
-
Click the "target" button (framed in red in the screenshot above) to display the Okta login page.

-
Enter your Okta credentials and click Sign In.
You are now logged into Okta.
© 2025 GridGain Systems, Inc. All Rights Reserved. Privacy Policy | Legal Notices. GridGain® is a registered trademark of GridGain Systems, Inc.
Apache, Apache Ignite, the Apache feather and the Apache Ignite logo are either registered trademarks or trademarks of The Apache Software Foundation.

